One of the main concerns from users of process safety systems is how to effectively protect the SIS against unauthorized changes of the safety logic. The traditional protection approach is based on a key switch on the safety PLC; before somebody can alter the safety logic, the key switch must be placed in the proper position.
While the key switch approach enforces physical presence before the safety logic can be modified, it has several drawbacks. The main issue is that end users could inadvertently leave the key switch in the unprotected position. Adding additional layers of security helps build a stronger, defense-in-depth approach.
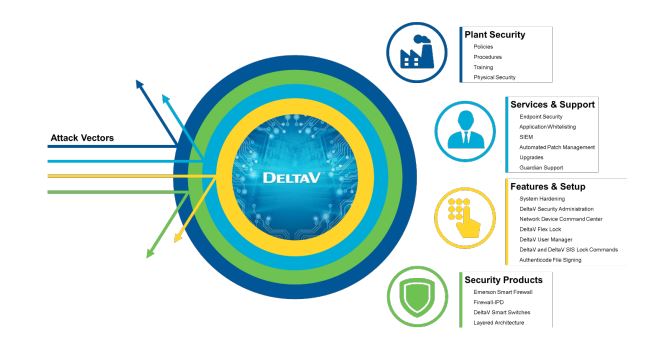
Click here to visit Emerson’s DeltaV SIS and Cybersecurity White Paper and learn defense-in-depth strategies for protecting safety systems.
Better protection with software-based security
A more secure approach is to implement two-step security, where the key switch is only a permissive for unlocking the logic solver. Moving the key switch does not automatically unprotect the logic solver; a user with proper system credentials must also send a command from a workstation before the safety logic can be modified.
The software component of this two-step defense approach enables the automatic re-lock of the CHARMs Smart Logic Solver (CSLS) to protect it regardless of the position of the key switch. While the key switch for the CSLS is in the permissive position, the safety user can send a timed unlock command from the workstation where the duration of the unlocked state is specified. The permissive key can immediately be switched back to the secure position. Only after this time expires, the CSLS is automatically returned to the locked state.
The value of a multi-layered security approach
While preventing unauthorized changes in the safety logic is paramount, there are other changes that must also be protected against. Table 1 describes the protection mechanisms available in DeltaV™ SIS and compares them with the typical protection available in traditional safety systems.
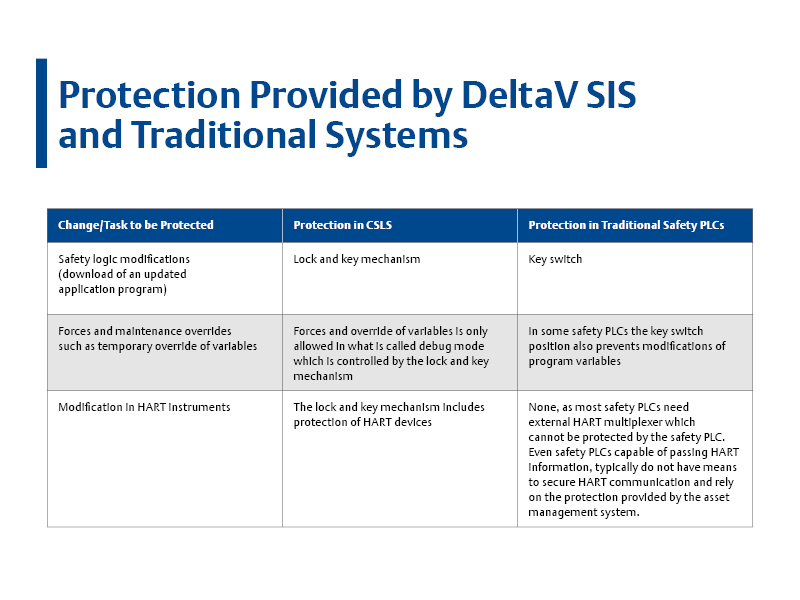
Protection provided by DeltaV SIS and traditional systems
The lock and key mechanism in the CSLS is not the only protection against unauthorized changes. DeltaV SIS uses a multi-layer approach where protections can be distributed among multiple components. For example, the embedded node acting as a proxy for all communication to and from the CSLS can also be locked in a similar manner to the CSLS. The lock mechanism of the proxy node (SZ controller) prevents logic server downloads even if the logic server is unlocked.
A defense-in-depth approach not only provides multiple lines of defense, but it also delivers more granularity for allowing or preventing different tasks. Let’s assume that an authorized change has been approved for a HART transmitter (e.g., the HART transmitter needs to be re-ranged due to changes in operating conditions). In DeltaV SIS, the timed unlock feature of the CSLS allows modifications in HART instruments while still preventing forces and maintenance overrides in debug mode. Since the proxy node can remain locked, configuration changes to the application program are also protected. As illustrated in Figure 1, instead of an all-or-nothing approach as with the traditional key-switch, multiple mechanisms provide the ability to disable only the required protections for authorized changes while still having other protections in place.
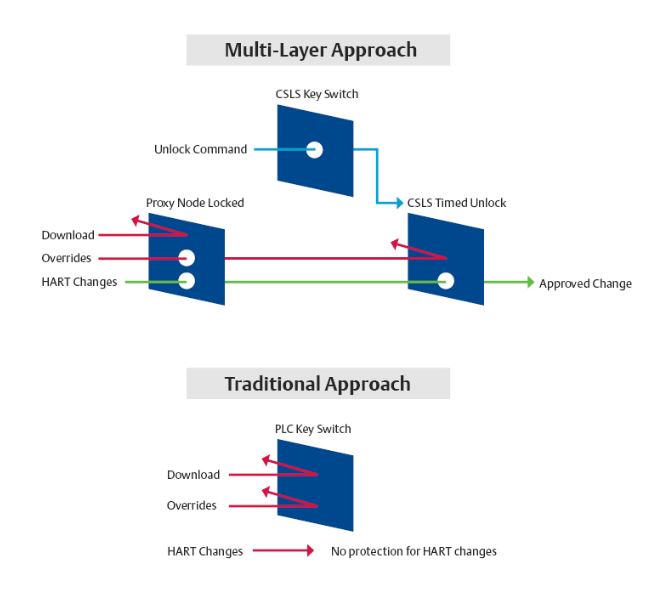
The multi-layered approach versus the traditional approach
Let’s now assume that a maintenance override needs to be implemented. On a single-protection approach (key switch), moving the key switch to allow for the override will also expose the safety logic. In DeltaV, the CSLS can be unlocked to allow the override while keeping the proxy node locked to prevent modifications on the safety logic. While unlocking the CSLS will expose the HART devices, since DeltaV SIS is a distributed system, the surface of exposure is lower than in a centralized system. A future blog will describe how a distributed system reduces the attack surface.
To learn more about Emerson’s DeltaV SIS and defense-in-depth solutions, please consult the DeltaV SIS and Cybersecurity whitepaper.
