As more and more processing plant personnel begin to work remotely in the wake of cultural changes from the global pandemic and an acceleration in plants’ digital transformation initiatives, there is probably no topic more deserving of attention than cybersecurity. Fortunately, industry groups have recently increased focus on this critical topic, releasing guidelines and standards such as those from IEC 61511—the standard for safety instrumented systems (SIS) in the process industries.
But guidelines and standards are just a starting point. The true measure of a cybersecure SIS is in how well those standards are implemented, and in that domain, users have a great deal of flexibility, for better or worse. This is where the help of experts can be invaluable, and, fortunately, Emerson’s Neil Peterson and Sergio Diaz have offered some much needed guidance in a recent article in Chemical Processing magazine.
In their article, Sergio and Neil share five essential tips for SIS cybersecurity. The tips are built around the requirement from IEC 61511 that organizations perform periodic cybersecurity risk assessments. Neil and Sergio share an explanation of how that requirement can often cause complications for cybersecurity teams,
“The IEC 61511 standard only provides a high-level description of cybersecurity assessments and refers to other standards such as ISA/IEC 62443 for guidance. One frequent result of the lack of details about cybersecurity assessments in IEC 61511 is that many organizations think they can check boxes on a security assessment more easily if their system is “air-gapped.” The result is often an inadequate assessment, leaving vulnerabilities in the SIS’s defenses.”
System architecture matters
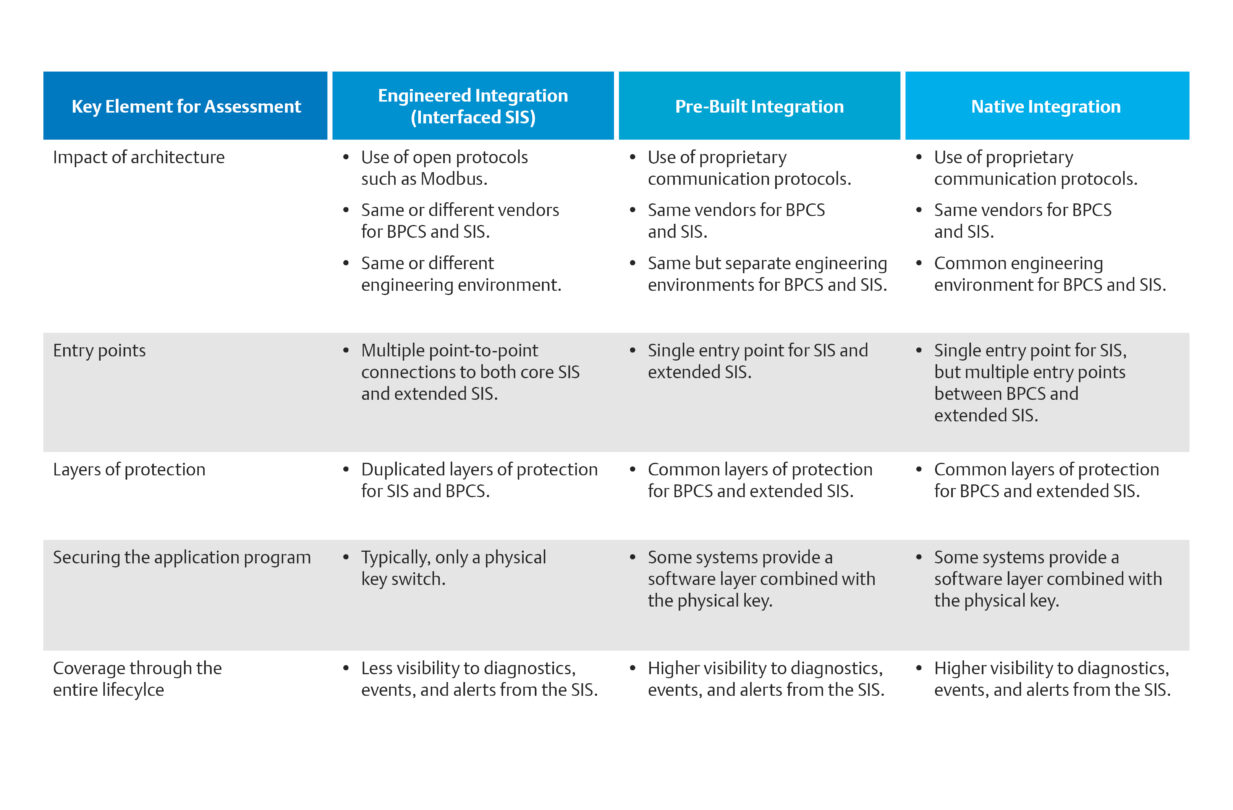
The authors explain that few if any systems today are truly air-gapped. At the very least, systems need to be connected periodically to outside sources for patching and updates. Instead, Sergio and Neil recommend three more common architectures: engineered integration, pre-built integration, or native integration. Using these architectures as a baseline, the authors present some strategies to help teams perform more effective assessments.
Sergio and Neil explain that architecture is the starting point for evaluating systems. Whether the SIS and basic process control system (BPCS) are separate or integrated, every system will have unique concerns the cybersecurity team needs to consider.
Lock down entry points
Every system needs to be examined for points of entry and have those entry points locked down. External systems such as asset management, process information management, safety lifecycle management, and more can all be potential entry points and must be secured. As Neil and Sergio explain,
“Each connection must be evaluated for cyberthreats across the entire connection.”
Using the connection between the SIS and BPCS as an example, they show how there are actually three potential targets: the SIS, the BPCS, and the interface between the two. All of these potential entry points must be properly secured.
Cybersecurity is not “set-and-forget”
Installing cybersecurity solutions is not an end point. As Neil and Sergio explain, cybersecurity teams must evaluate their solutions across the lifecycle of the equipment. In addition, the teams must also be aware of what those systems are finding across their lifecycle. As the authors explain,
“[Defense in depth] is only as valuable as the team’s awareness of what the defense systems are reporting, and that awareness depends on correct implementation and operation of the safety system. Cybersecurity assessments should evaluate the way the security team interacts with the system, ensuring they have instant visibility of issues, along with strict rules and restrictions for interacting with safety systems.”
Five critical recommendations can help security teams perform better assessments.
Sergio and Neil share a number of other critical tips for improving cybersecurity assessments. And many of these solutions are implemented more easily, intuitively, and effectively on integrated control and safety systems like the DeltaV™ distributed control and safety systems.
You can explore more of the recommendations from Neil and Sergio, including the other assessment guidelines by reading the article in its entirety at Chemical Processing. While you’re here, I’d love to hear any recommendations you have for securing control and safety systems. Feel free to leave comments below to share your thoughts with your fellow readers!





